Features
Features
Derby can be deployed in a number of ways and in a number of different environments. The security needs of the Derby system are also diverse. Derby supplies or supports the following optional security mechanisms:
-
User authentication
Derby verifies user names and passwords before permitting them access to the Derby system. See Working with User Authentication.
-
User authorization
A means of granting specific users permission to read a database or to write to a database. See User Authorization.
-
Disk encryption
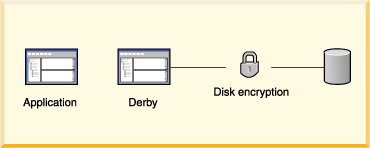
A means of encrypting Derby data stored on disk. See Encrypting Databases on Disk.
-
Validation of Certificate for Signed Jar Files
In a Java 2 environment, Derby validates certificates for classes loaded from signed jar files. See Signed Jar Files.
Figure 10. Some of the Derby security mechanisms at work in a client/server environment
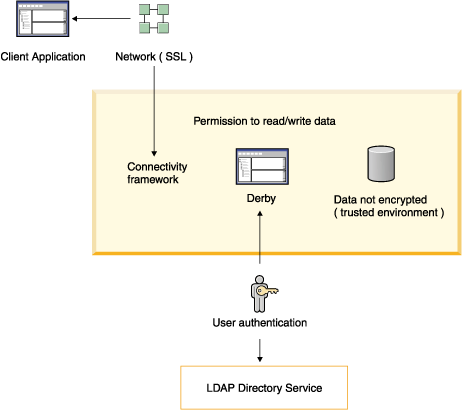
Figure 11. Another Derby security mechanism, disk encryption, protects data when the recipient might not know how to protect data. It is useful for databases deployed in an embedded environment.
Previous Page
Next Page
Table of Contents
Index

